Zero Knowledge Proofs: What They Are, How They Work, and Why Your Business Needs Them
Discover how zero-knowledge proofs prove compliance, block fraud, and slash breach costs without revealing customer data.

TL;DR
- Enterprises are drowning in sensitive data yet face soaring breach costs, fines, and cyber-insurance premiums.
- Zero-knowledge proofs (ZKPs) let a company prove a claim–e.g., “customer is over 18” or “transaction meets AML limits”–without exposing the underlying personal data, dramatically reducing liability.
- Cryptographic proofs replace raw records in audits, partner integrations, and AI pipelines, trimming storage, transfer, and compliance overhead while keeping regulators satisfied.
- ZKPs remove cross-border transfer friction by sending anonymised attestations instead of GDPR-regulated data, and they block fraud or botting by issuing non-reusable, verifiable credentials.
- Verifiable Private Identity can supply industry-leading, millisecond-speed ZKP infrastructure that makes privacy-preserving identity practical at enterprise scale.
- Together, ZKPs and VPI convert data from a combustible liability into a controllable asset, enabling secure, regulation-ready growth across Web3 and traditional markets alike.
The Cost of Data Hoarding: Breaches, Fines, and Rising Compliance Pressure
Most executives are keenly aware of the compelling narrative of data. Marketing teams request click-streams, every new AI agent demands progressively larger training sets, and modern analytics platforms promise that more data will yield more detailed insights. Competitive fear perpetuates the collection cycle: organisations worry that failing to capture data will place them at an analytical and competitive disadvantage. However, the lure of data hoarding quickly fades when large repositories of data become breach targets, thus putting users and their personally identifiable information (PII) at high risk. Consequently, new regulations now require or incentivise rigorous protection of user data. Users’ right of access to, rectification of, and erasure of their data must be upheld by all stakeholders.
The EU’s General Data Protection Regulation (GDPR) and other data protection regulations and compliance standards are often difficult and costly to meet: the GDPR has issued over six billion USD worth of fines since its creation in 2018. From the complexities of cross-border transfers to steadily increasing cyber-insurance premiums–executives recognize the challenges of hoarding data. In particular, the risk of a data breach is omnipresent and financially consequential (IBM’s 2024 report puts the average cost of a data breach at 4.88 million USD).
Breach Risks and Attack Avenues:
Malicious insider attacks:
- Phishing and credential theft accounted for the most expensive data breaches, averaging 4.99 million USD. Attackers bypass technical controls by exploiting trust: A “VPN password expired” email, a help-desk voice call, or a barrage of MFA push notifications may induce employees into granting access.
Shadow data:
- Unmanaged copies of data created by processors, suppliers, and interns significantly expand the surface of attack. IBM reported that shadow data was involved in a third of all breaches, demonstrating the difficulty of securing assets that are not formally inventoried.
Third party risk:
The recent announcement of Vodafone GmbH’s 50 million USD fine highlights the pain of inherited risk. Germany’s federal privacy authority fined the telco over 50 million USD because partner agencies failed to meet Article 28 GDPR obligations. Outsourcers, cloud providers and SaaS vendors extend your information system perimeter into environments you neither own nor audit daily. When they fail, you also pay. Controllers are now fully liable for lapses by their processors.
Regulatory pressures
The regulatory burden attached to personal-data stewardship has become both expansive and expensive. Because the GDPR applies extraterritorially, the mere possession of a single EU resident’s e-mail address can subject an organization to 99 separate compliance obligations and potential fines of up to 4 percent of global annual turnover. Exercising the GDPR’s data-subject rights–access, rectification, and erasure–generates service tickets that must be handled by legal, IT, and customer-support staff; and large retailers now receive them by the thousands each month. Excessive data no longer represents unqualified value; instead, it constitutes a highly volatile liability.
How can ZKPs benefit your business?
Zero-knowledge proofs (ZKPs) enable businesses to satisfy audits, partner demands, and AI models without ever exposing or storing the underlying sensitive data.
What are ZKPs and How Do They Work?
ZKPs are cryptographic protocols that let one party (the prover) convince another party (the verifier) that a statement is true without disclosing anything beyond the truth of that statement itself. They help companies satisfy business queries, partner demands, and regulatory auditors with mathematically verifiable proofs rather than raw records. In other words, using ZKP solutions, companies could extract the same insights while substantially reducing the volume of data that must be moved, stored, processed, insured, and defended.
Although zero-knowledge systems appear under various technical labels–such as zk-SNARKs, zk-STARKs, and Bulletproofs–their operating principle is straightforward:
- The organisation first expresses the policy it wishes to demonstrate (for example, “the applicant is over 18” or “this transaction meets anti-money laundering requirements”) as a series of basic mathematical steps.
- The software then produces two long-lived codes: one for creating proofs and one for verifying them.
- When the holder inputs the confidential data, the program generates a very small digital receipt–the proof–that confirms the policy has been met.
- Any authorised party can read this receipt with the verification code and obtain certainty that the rule was satisfied, yet the underlying data never leaves the holder’s control.
Zero-Knowledge Proof Example
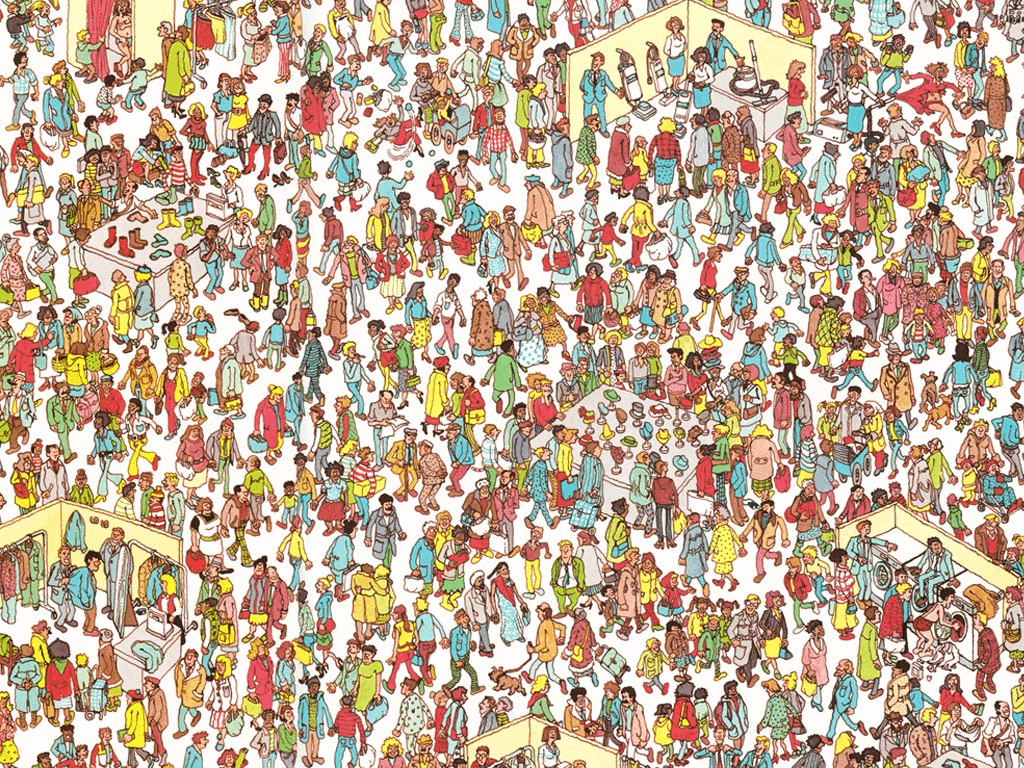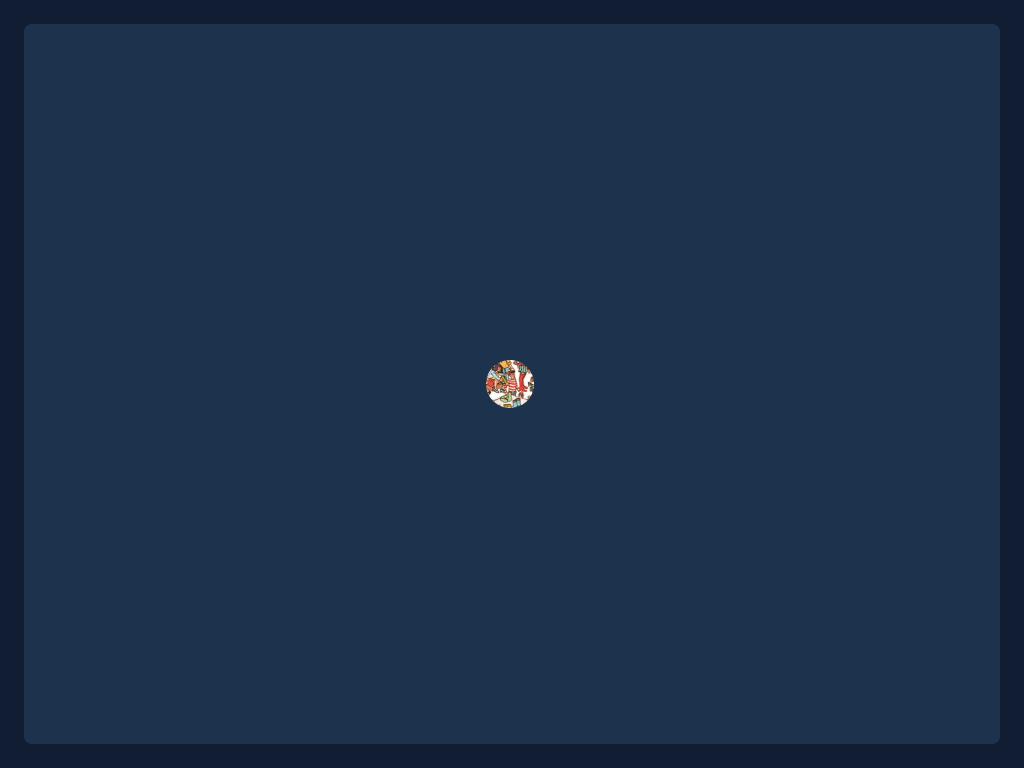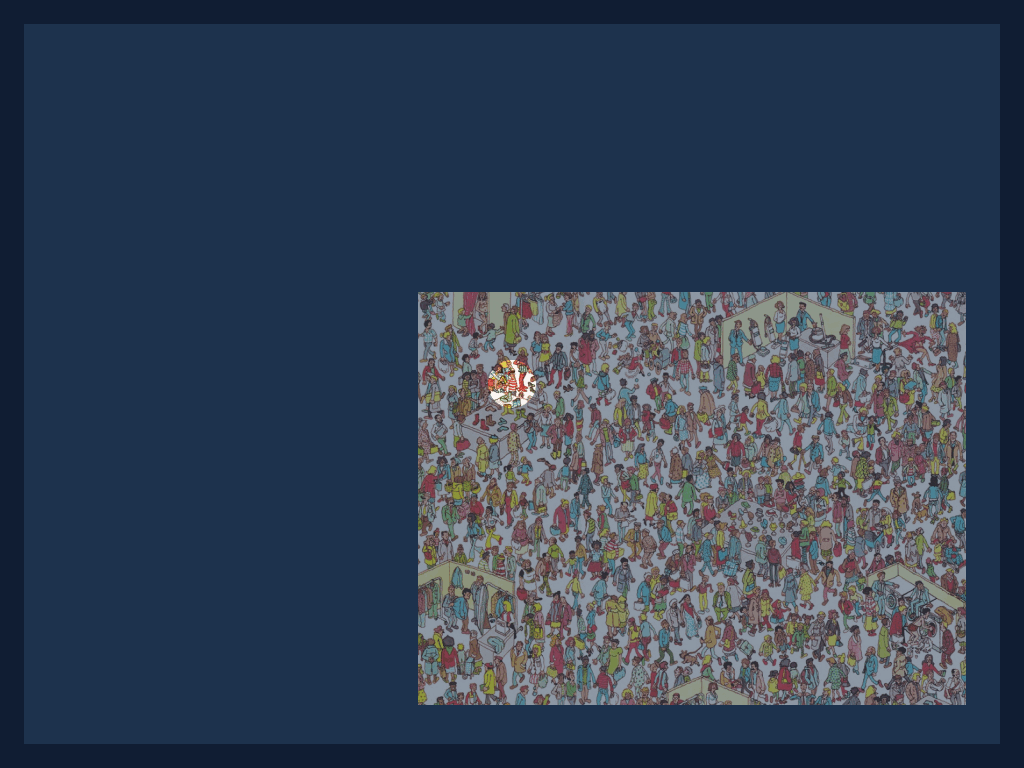
Imagine the familiar “Where’s Wally?” scene: an illustration densely packed with thousands of characters. The employee who has already located Wally (the prover) must convince a colleague (the verifier) that the search is complete without disclosing where Wally is, who stands next to him, or any other detail on the page. The prover places an oversized sheet of paper on top of the picture and cuts a single, coin-sized hole. By sliding the sheet until Wally’s face appears in the opening, the prover demonstrates knowledge of Wally’s position. The verifier sees only Wally through the hole–nothing else–and therefore gains no additional information about the broader crowd.
In effect, zero-knowledge proofs allow a party to deliver a reliable “yes” or “no” answer while keeping all sensitive information private. For businesses, the technique translates into proving that a customer is over 18, solvent, or free of sanctions, without ever handing over the underlying personal data.
How Zero-Knowledge Proofs Reduce Breach Impact and Cyber-Risk
Because the verifier never actually touches and accesses the underlying data, ZKPs effectively decouple the truth from the access to information and thus vastly reduce the need for many companies to store PII. This property addresses the pain points discussed above–credential theft yields no exploitable records, shadow copies become unnecessary, and controllers can demand compact cryptographic attestations from vendors rather than raw datasets, thereby containing liability when a downstream processor fails. Ultimately, as companies empowered by ZKP solutions replace vast storages of PII with proofs, they leave external attackers little to steal even if their data systems are compromised.
How Zero-Knowledge Proofs Power Cross-Border Data Transfers
ZKPs bypass the complex environment of Standard Contractual Clauses, Transfer Impact Assessments, and on-going monitoring that the Schrems II ruling and other regulations require by ensuring that what crosses borders is not personal data at all.
For example, suppose that a European bank must inform its New York broker that an account holder meets anti-money-laundering thresholds. Instead of forwarding the customer’s passport scan and transaction history, the bank generates a zk-proof that proves that “the account’s risk score ≤ 3” under a jointly agreed model. The broker verifies the 700-byte proof locally; no identifying fields ever leave the EU, so GDPR’s Chapter V ceases to apply. Because the statement is mathematically bound to the model parameters, the New York office gains the same assurance it would have obtained from raw documents, yet the legal classification of the payload changes from “personal data” to “irreversibly anonymized artifact,” resulting in dramatically lower liability exposure during cross-border audits.
How Non-reusable ZK Credentials Stop Fraud and Botting
Many forms of fraud and botting rely on cheap replication of credentials (such as emails) and on forged documents that slip through optical checks. Zero-knowledge architectures upend these dynamics by making every required attribute provable yet non-reusable. Consider a ticketing platform besieged by bot farms that acquire large amounts of concert tickets immediately upon release. During registration each human customer receives a one-per-person cryptographic credential from a trusted issuer (a bank, telco, or government ID service). When the sale opens, the customer submits a zero-knowledge proof that “this credential exists in the issuer’s registry and has not been used in the current drop,” yet reveals neither name nor credential number. The platform verifies the 800-byte proof in milliseconds, and cloned or purchased accounts cannot mint additional proofs because the issuer will sign only once per real individual. The same mechanism extends to age-restricted storefronts and gaming sites: instead of uploading a scan of a driver’s licence–which under-age users can manipulate and criminals can appropriate–the buyer produces a range proof that “date of birth ≤ 2006-01-01.” In every case, the verifier gains binary assurance while potential attackers gain nothing reusable, therefore shrinking charge-backs, eliminating counterfeit documents, and leaving fraudsters and botters with no viable angle of attack.
T3-Powered Zero-Knowledge Proofs in Verifiable Private Identity (VPI)
Think of a verifiable private identity (VPI) as a digital passport you keep in your own wallet, not in a corporate database. It bundles two pieces: (1) a decentralised identifier, a long-lived public key that points to you, and (2) a set of verifiable credentials–signed statements from issuers such as banks, exchanges or government registries that you are over 18, pass AML screening, or hold accredited-investor status. The magic is that the credentials never have to be shown. Instead, when a regulated exchange asks for KYC, your device produces a zero-knowledge proof that “the holder of this DID owns credentials A, B and C, none are revoked, and this DID has not been used elsewhere today.”
The exchange verifies the kilobyte-scale proof in milliseconds, a performance made possible by Terminal 3’s high-speed ZKP platform, then logs the result for Travel-Rule compliance while learning nothing else–neither your name, address, nor passport number. Every subsequent trade or cross-chain transfer attaches a fresh proof, so bots cannot replay old tickets and fraudsters cannot forge documents. Because all personal data stays client-side and only proofs circulate, custodians avoid breach liability, regulators get cryptographically audited compliance, and institutions finally obtain the trust surface they need to scale digital-asset liquidity.
Conclusion
Zero-knowledge proofs transform data from a combustible liability into a controllable asset. By decoupling truth from disclosure, they let firms answer auditors, partners, and machine-learning pipelines with compact attestations rather than warehouses of personal records. Credential-theft yields nothing, shadow copies evaporate, and inherited vendor lapses surface immediately through cryptographic checks. The procedural complexity of cross-border transfers can be avoided, continuous proofs replace quarterly paper audits, and bad actors cannot generate valid proofs from forged documents or duplicate accounts.
Terminal 3’s industry-leading ZKP platform proves that these benefits are available at enterprise speed and scale today, overcoming the latency constraints that have historically limited zero-knowledge adoption. What began as a pragmatic way to reduce breach impact and compliance spending therefore evolves into a strategic platform play: the same technology underwrites high-throughput blockchains, privacy-preserving analytics, and verifiable on-chain identities. In short, zero-knowledge proofs constitute a foundational technology for a scalable, trustworthy, and regulatory-compliant Web3 ecosystem.
About Terminal 3
Terminal 3 is a Hong Kong-based Web3 startup building data infrastructure for a decentralized future. The company’s solutions are an alternative to centralized data systems that deprive users of privacy and saddles enterprises with compliance and security concerns. Terminal 3 leverages decentralized and privacy-enhancing technologies to empower an equitable Web3 where fully private user data is freely composable. The company’s founders are successful corporate executives and entrepreneurs, who have built, scaled, and transformed some of the world’s most important companies. Terminal 3 is also backed by world-class investors including Illuminate Financial, CMCC Titan Fund, Animoca Brands, IDG Blockchain, Progression Fund, Cherubic Ventures, 500 Global, Consensys Mesh, Bixin Ventures, BlackPine, Hard Yaka, and Bored Room Ventures.
For more information, visit our: Official Website | X | LinkedIn




